Session Hijacking
What is Session Hijacking? Most Web applications store information of the user ( the classic example is the shopping basket) in the HTTP session. But also the basic user information. So, whenever someone else knows the ID of the session, he can impersonate the victim and act on behalf of him/her.
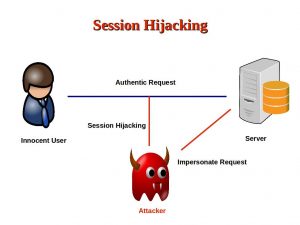
The following image shows the attack (image by A. Mitra)
Octopus protects
But there exist a few techniques to identify if such an attack is in progress for a certain session. And this technique is implemented within the Octopus framework (from v0.9.7 on)
You don’t have to do anything specific to activate this features, it is on by default.
When such an attack is detected, the attacker gets a blank page with the message that access was denied due to a Session Hijacking attack detection. But also the actual victim can be informed of the attempt to take over his/her session.
See the following short video to see the feature in action.
The code used to create the video is on GitHub.
Have a look at the parameter session.hijacking.level to configure the feature in case you have issues or want to deactivate it.
Conclusion
With the Session Hijacking protection, Octopus tries to make the applications as safe as possible. It is only one of the security features it has. You saw also in the video that the session ids are changed when the user logs on and logs off, just as OWASP recommends it.
Have fun.
